Cybercriminals are continuously adapting to bypass security defenses, and one of the latest techniques they’ve employed is the use of ZIP file concatenation. This strategy takes advantage of the way different ZIP readers process concatenated ZIP files to embed malicious payloads that evade detection. Here’s an overview of how this tactic works and how it is being exploited by attackers.
What is ZIP File Concatenation?
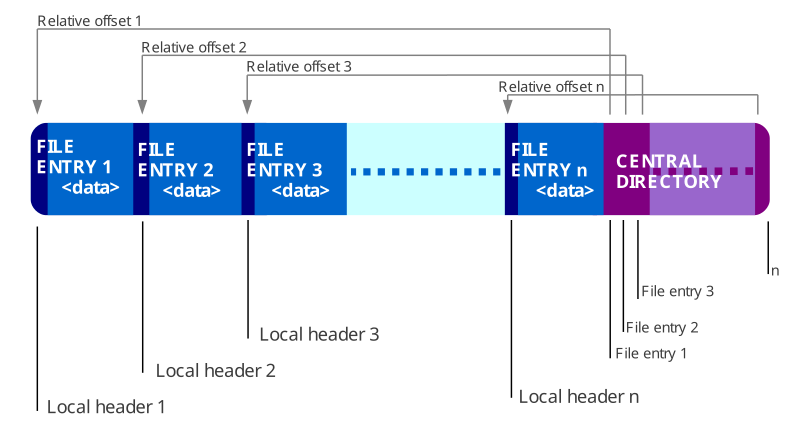
ZIP files are widely used for file compression and bundling multiple files into one convenient archive. The ZIP format’s flexible structure makes it an attractive target for attackers looking to evade security measures. A typical ZIP archive contains three main parts:
- File Entries: The compressed files and folders within the archive.
- Central Directory: An index of the entire archive, making it easy to access and extract files.
- EOCD (End of Central Directory): The metadata that tells ZIP readers where the central directory starts.
By exploiting the differences in how various ZIP readers process these structures, attackers can hide malicious files within certain parts of the archive that not all readers will access, leading to undetected attacks.
ZIP Readers and Their Differences
The behavior of popular ZIP readers—such as 7zip, WinRAR, and Windows File Explorer—varies when handling concatenated ZIP files, which is what makes this evasion technique effective. Below is a comparison:
| Program | Strengths | Use Case |
|---|---|---|
| 7zip | Open-source, supports many formats, efficient compression | Developers, cybersecurity professionals |
| WinRAR | Reliable, error recovery features | General and professional users |
| Windows File Explorer | Built-in, simple ZIP handling | Casual Windows users |
How Concatenated ZIPs Work
ZIP concatenation involves combining multiple ZIP archives into a single file. This results in a file that looks like a single archive, but actually contains multiple central directories. These discrepancies in central directory handling are what attackers use to hide malicious content.
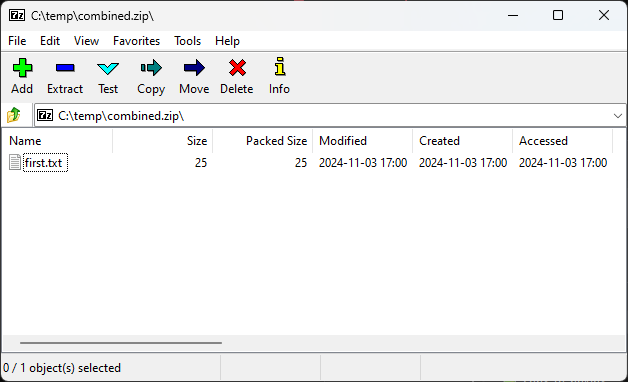
For example, an attacker might concatenate two ZIP files (pt1.zip and pt2.zip), but when opened with certain tools, only the files from the second archive are visible.
- 7zip: Only shows the first archive, displaying the benign content, but warns that there is data after the archive’s end.
- WinRAR: Displays the contents of the second archive, which includes the malicious payload.
- Windows File Explorer: May fail to open the concatenated file or reveal the malicious content when the file extension is altered to .rar.
This subtle manipulation of file structure enables attackers to target specific users based on the ZIP reader they use.
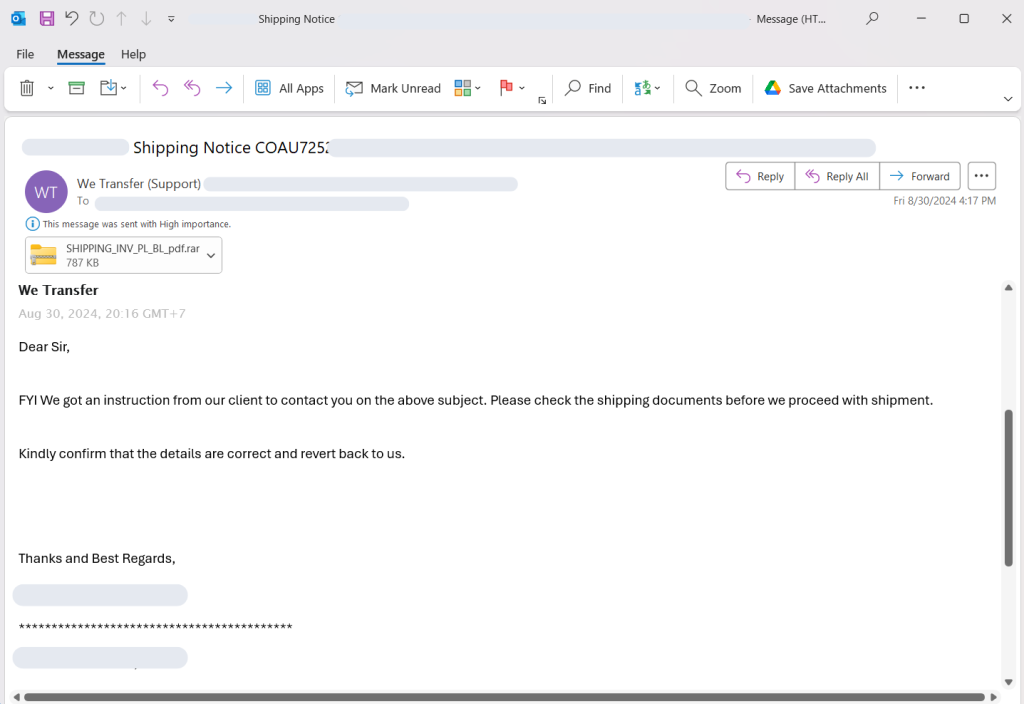
Real-World Example: Trojan Delivered via Concatenated ZIP
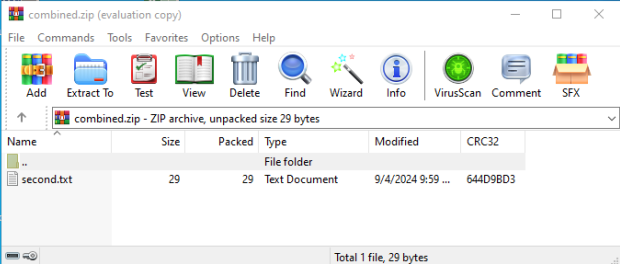
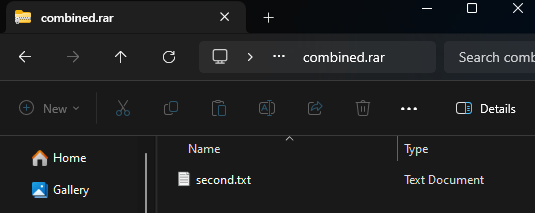
In a recent attack, a Trojan was disguised as a legitimate shipping document and distributed via a concatenated ZIP file attached to a phishing email. The email, marked “High Importance,” urged the recipient to review the shipping documents.
- 7zip: Opening the file with 7zip displayed a harmless-looking PDF, masking the Trojan payload.
- Windows File Explorer/WinRAR: These tools exposed the Trojan executable hidden in the second part of the archive, alerting the user to the danger.
The Trojan, identified as a variant of SmokeLoader, is a malicious executable that uses the AutoIt scripting language to automate further attacks, such as downloading and executing additional malware.
Evasion Continues: Why It Works
Attackers know that many security solutions rely on popular ZIP tools to parse archives. These tools often fail to unpack concatenated files fully, leaving hidden threats undetected. The attackers exploit this gap to deliver malware that bypasses most detection systems.
The Recursive Unpacker: Detecting Hidden Threats
Traditional security tools often miss the hidden payloads in concatenated archives. However, Perception Point’s proprietary Recursive Unpacker algorithm addresses this issue. By recursively analyzing every layer of a ZIP file, the tool ensures that even deeply concealed malware is uncovered, allowing for comprehensive threat detection.
Conclusion
The use of ZIP concatenation for evading detection is a sophisticated tactic employed by attackers to bypass security solutions. By manipulating how ZIP readers process files, malicious actors can hide payloads and target specific systems. As this technique continues to evolve, it’s crucial for organizations and individuals to stay vigilant and ensure their security tools can handle such advanced evasion methods.
Stay safe, and always be cautious when handling email attachments or unfamiliar archives!
Source : Evasive ZIP Concatenation: Trojan Targets Windows Users | Perception Point