Introduction
In the fast-paced world of cybersecurity, a well-defined Incident Response (IR) plan is essential for organizations to manage and mitigate cyber threats effectively. With the rising complexity of cyberattacks, an incident response strategy helps businesses to manage impact, minimize damage, and restore normal operations swiftly. This article breaks down the key components of a successful incident response framework and emphasizes the importance of prioritizing cyber incidents.
What is Incident Response?
Incident response is a structured approach to managing the aftermath of a security breach or cyberattack. The primary objective is to identify, contain, and eliminate the threat while minimizing damage and ensuring business continuity. A strong incident response plan ensures that companies are prepared to act quickly and effectively when a cyberattack occurs.
For an organization to be truly ready to respond, it must have:
- A well-defined plan
- Trained personnel
- The necessary tools
It’s also crucial to have proper coordination across various business units and to practice handling cyberattacks through Tabletop Exercises (TTXs), which help teams prepare for real-world scenarios.
The PICERL Lifecycle
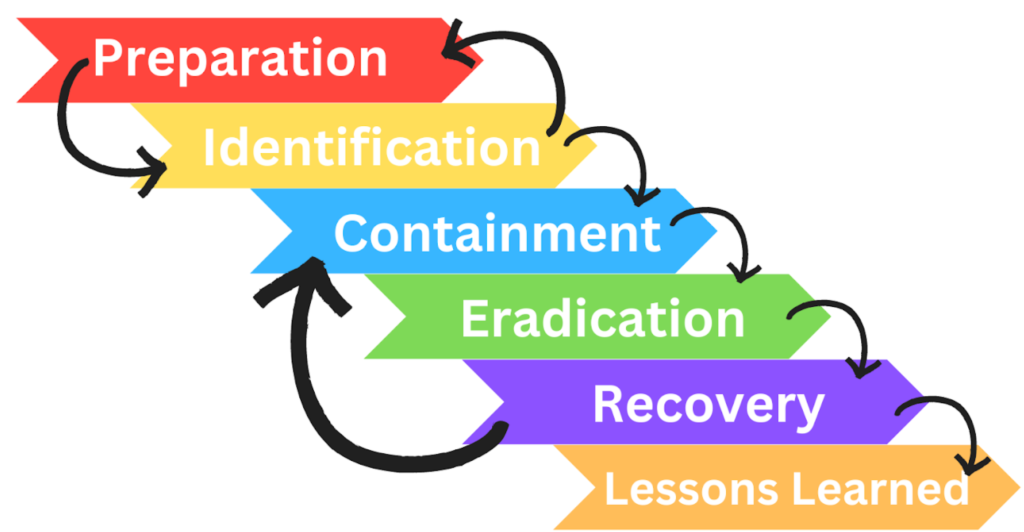
The PICERL lifecycle is a widely accepted framework for handling cybersecurity incidents. It consists of six critical phases that guide an organization from preparation to post-incident improvements:
- Preparation
- Develop and review incident response strategies.
- Train the Cyber Incident Response Team (CIRT).
- Ensure documentation and communication plans are in place.
- Identification
- Detect and identify incidents through security tools like SIEM and EDR.
- Understand the scope and impact of the incident.
- Containment
- Prevent further damage through short-term and long-term containment strategies.
- Eradication
- Remove all traces of the compromise, including malware and vulnerabilities.
- Recovery
- Restore affected systems and operations, ensuring proper integration with existing security controls.
- Lessons Learned
- Evaluate the incident to improve future response plans and enhance security measures.
Incident Priority and the Priority Matrix
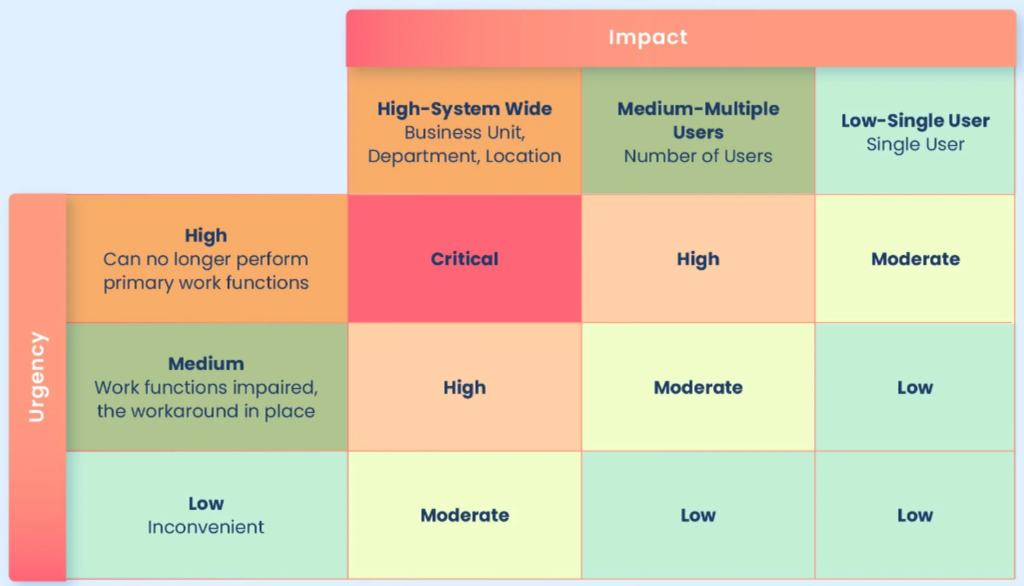
Determining the priority of a cyber incident is crucial for an effective response. The impact of the incident directly influences how resources are allocated and how quickly the team can respond.
The Priority Matrix helps categorize incidents based on urgency and impact, providing a quick reference for the response team. By assessing the incident’s potential to disrupt critical business operations, companies can prioritize their response effectively.
The Importance of Collaboration Between Teams
One of the key lessons learned from effective incident response is the importance of collaboration between different teams, including the Privacy and Incident Response teams. In cases like data breaches, it’s essential to ensure seamless coordination between the teams responsible for privacy and those handling the security aspect of the breach.
Conclusion
An effective Incident Response plan is not just about reacting to cyberattacks but proactively preparing for them. By understanding the PICERL lifecycle and using tools like the Priority Matrix, organizations can better manage their response efforts, ensuring minimal disruption to their operations. Continuous improvement through post-incident reviews ensures that companies are always prepared to face the evolving threat landscape.
By investing time and resources into developing an efficient incident response strategy, organizations can enhance their resilience against cyber threats and safeguard their business continuity.
How is your organization preparing for cybersecurity incidents? Are you using a priority matrix to manage incident response? Share your thoughts in the comments below!